It's not quite complete without code on the password reset page to tell you that you can't reuse your password.
And label the text box "username" when it only accepts email address.
Don't forget to have hidden password requirements and secretly truncate any password longer than 12 characters.
Well yeah, if you don’t truncate the password to 12 chars how will you fit the plaintext in a memory efficient fixed latin1 CHAR column that only accepts letters, numbers, and underscores
/s
And then validate the email with a custom regex that definitely doesn’t account for all the valid syntax permutations defined by the several email-oriented RFCs
You guys are evil - who shat on your pillow??
Hearsay
I've had that before and I'm very confident the password was correct - my theory is that they'd changed how non-ASCII characters like £ were handled and their code only half recognised my password.
As a non programmer, is the joke that humans will retype their password assuming that they made a typo?
If so, sick indeed.
The guy coding made it so, on your first attempt, even if you answer correctly, it will tell you your login failed due to incorrect username or password, to joke about how it feels like you always get it wrong on the first try
The logic is bugging me, though. It should be if isFirstAttempt || !isPasswordCorrect
I understand the meme is trying to convey in spite of being correct to still return an error, but then it doesn't account for when the password is actually incorrect.
That defeats the brute-force attack protection…
The idea is that brute-force attackers will only check each password once, while real users will likely assume they mistyped and retype the same password.
The code isn’t complete, and has nothing to do with actually incorrect passwords.
Like the other person said, it's not meant to always fail the first time you enter any password.
It is meant to fail the first time you enter the correct password.
Yeah, hackers have automated tools and they will, of course, only try each password once.
I would assume that I was being phished and the attacker wanted me to re-type the password to verify that it's correct.
Well, I sometimes input the same password 15-times in a row, and it works only on the last try. ¯\_(ツ)_/¯
I swear this is what some websites do
Cell phone lock screens too.
Also USB cords
This could actually work though lol, it's genius
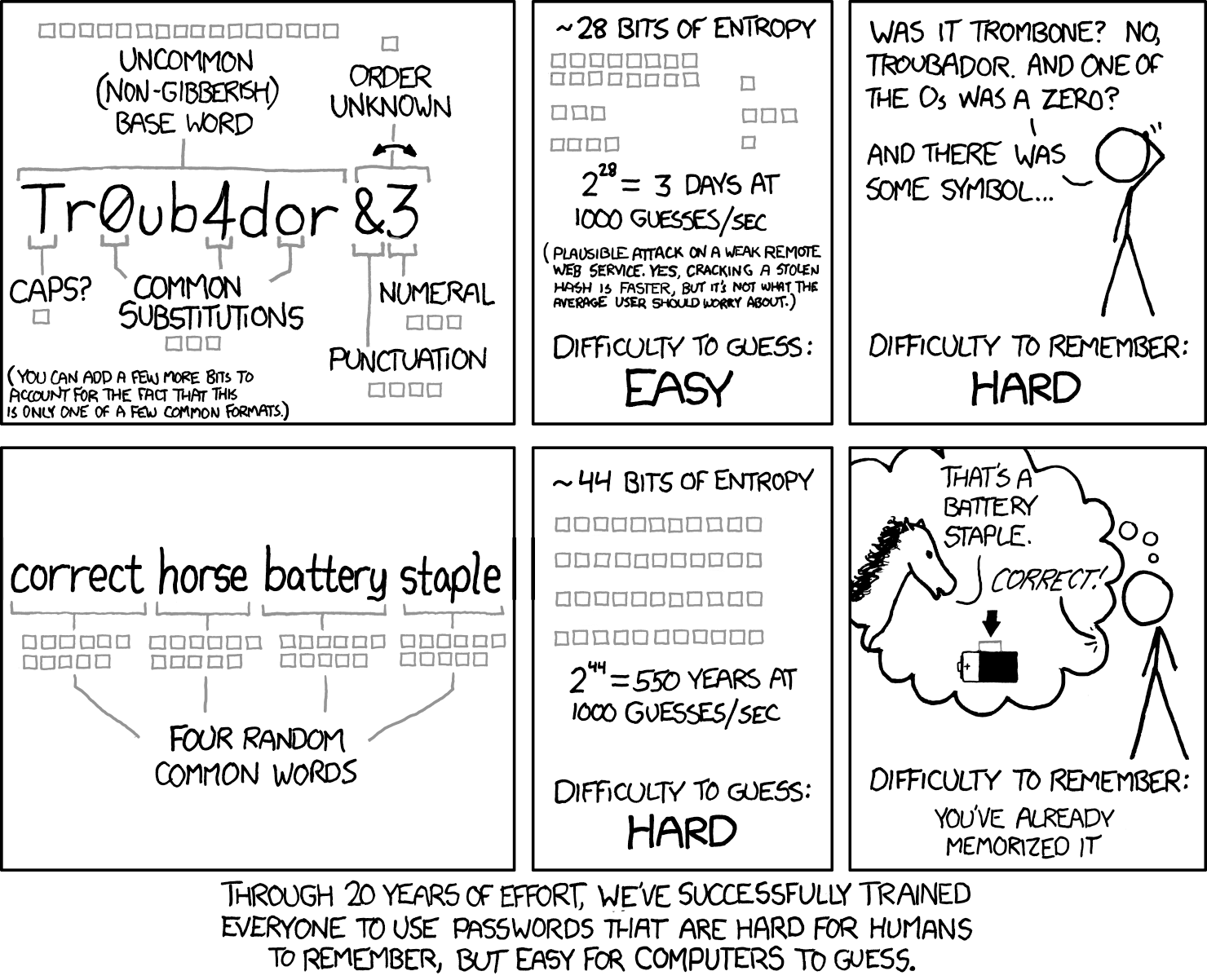
Rainbow tables and presumably newer stuff I haven't heard of make this sort of thing weaker than it used to be
Salting makes rainbow tables pretty much useless, and salting has been a standard practise for a few decades now.
How does a rainbow table help here? They're more for decoding unsalted encrypted database tables, rather than for actually trying to login.
The rainbow table would have to include every four word combination. At around half a million words in the English dictionary, that's not a small number.
As another XKCD comic illustrates, it's cheaper to use a wrench.
Dictionary attacks have been around for a long time, but It's still quite strong especially if you throw in a number.
A fully random 8 character password has about 10^14 brute force combinations (assuming upper and lower case + the normal special characters). 4 words choosen at random from the top 3000 words (which is a very small vocabulary really) is 10^13 dictionary attack combinations, add a single number or account for variations in word style (I.e maybe don't always use camel case) and you've matched the difficulty. If you use 5 words it's 10^17 combinations.
A password manager and a hard password is a better idea but there are cases where you can't use a password manager (like the password to said manager).
Example of what My passwords are like :
%*7EfOLkN@6AP28!8Dl#
or potentially if allowed :
W@c2wYnN9J3xGcyc47#ZkHJvt&Hm%q&Ad0b&Xwz#jnl4Th%6UBexD16a$YBFc@svnVrCBxXP0EpwLp6%Gk*Lom%@Qq#DjY1zsf0CzIrHHqPc8gt4edDVsg!omj*kIsIJ
Good luck guessing my shit.
Amateur! Strong enough passwords are like:
ÕÚüd¸2stb½õ~jëv×Â/oyÓh²î´t¶»Ö°ÍðoNVRïé2Wc4'H,CâÞó_ökÅ,Kð¡X9ÄÀ.þTØÓoæ73d*ëÞ¢?²i"`צeÉçß,ÎÅëüS.¹([)ãÒÑêf9÷¿¢=@Á×ÅQÎÂßu¸Å(iRZµîw&ãR

That's the stupidest combination I've ever heard in my life! That's the kinda thing an idiot would have on his luggage!
Try this on for size :
`'�d+�t<�5mF�qrqcmv/�F��~��Yv�Om�/lK�RɏY%ɺP1�h�Ryl-�G/��m�ʰ�+^)��<>�itdkaz�q2HA*1�PK�D@{9�vN.<}�~ٕ�_�26IA/cHIn����1ĈҾܒl�I9$�vA��W¸ȶW"z�}θ�x�,>~�Ux�SJZ\�5ÀI��F}nLZT�;KӚq�&NQo32y7���0"^LÎs>��j!��V��k��2O<2W�ƽYcA#8�J�Of�pهZb�%1g�w�!k*h(ʶ73�@�CC�hUsԺe!_��dR�ٞpvG|.=4{v"&.��m=_�͚DZZף�aaZ��Cq�!sG1T3�=2lb,����^�镰n)Ld]��Ϯ
The one guy got grey hairs in-between slides lol
If they had the password right the first try, that isn't a brute force attack, thats a credential leak.
I think the author attempted first time login to be with the right password.
It should be that it rejects the password the first time it's entered correctly but accepts it on every subsequent try. That actually would provide some protection against like dictionary attacks and raw brute force attacks.
could also work in a brute force scenario, but first attempt would be not first attempt in a set amount of time but first attempt for each password by the user in a fixed amount of time
This is negging for auth.
That's actually pretty smart
Password managers say hi
Fine I'll just change my password to what I thought it should be.
*New password cannot match old password
Won't protect against an offline attack (just will confuse the hell out of the hacker) but might confound an online attack? Until someone gets wise and runs the tool a second time. Loving the chaotic neutral vibes here.
I remember in college editing OpenSSH source code to instead of return wrong password to a root shell prompt just to stop brute force attacks
Not to be pedantic but wouldn't it be IsFirstLoginWithAttemptedPassword or am I missing something?
no, since it first checks if the password is correct. if it is, display error message. if it is corrent and the second time, accept the password (code not in screenshot) but if the password is wrong, it doesnt check if it is the first attempt.
This is a really interesting idea, but a password manager would throw a wrench in it.
I'd assume my password was invalidated or stored incorrectly, so I'd reset, then I'd try to log in, wtf... this website blows.
took me a solid 30 seconds of re-reading to get the joke
Memes
Rules:
- Be civil and nice.
- Try not to excessively repost, as a rule of thumb, wait at least 2 months to do it if you have to.
